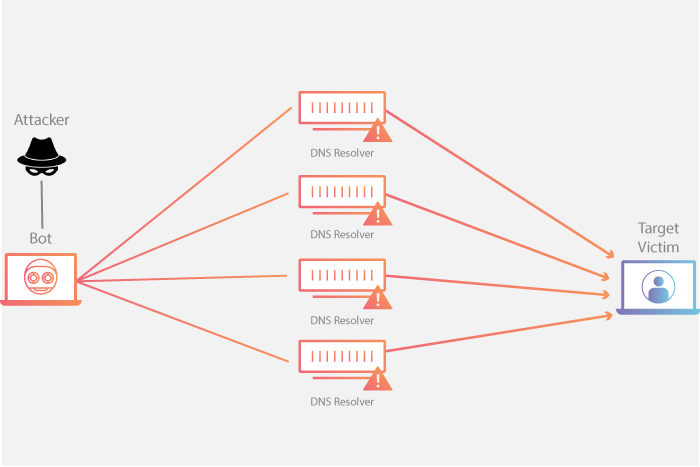
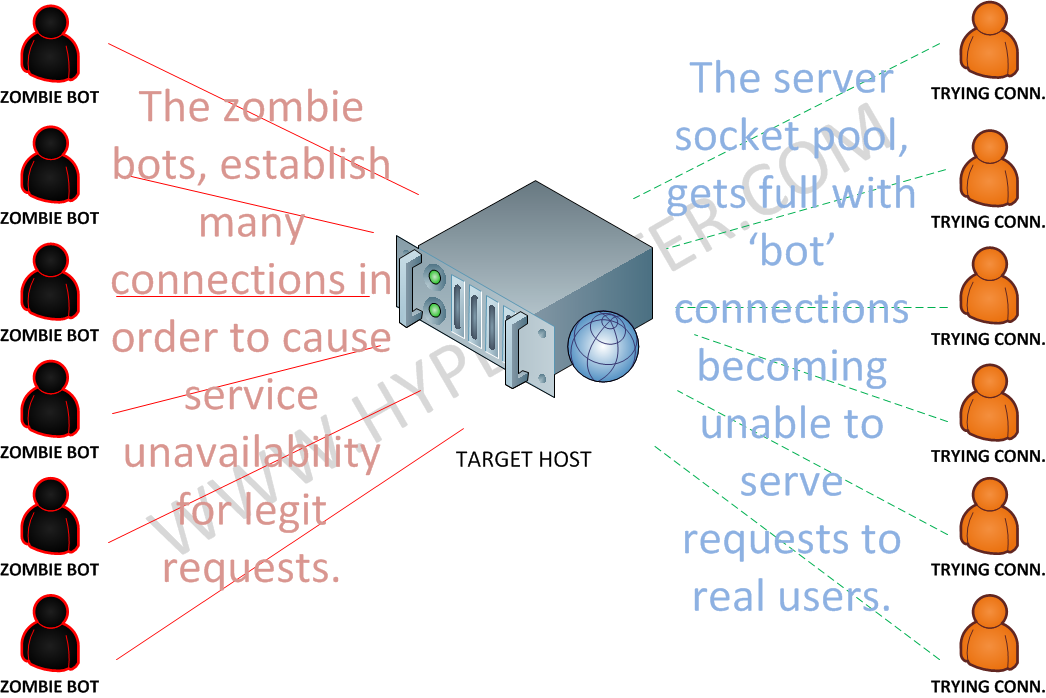
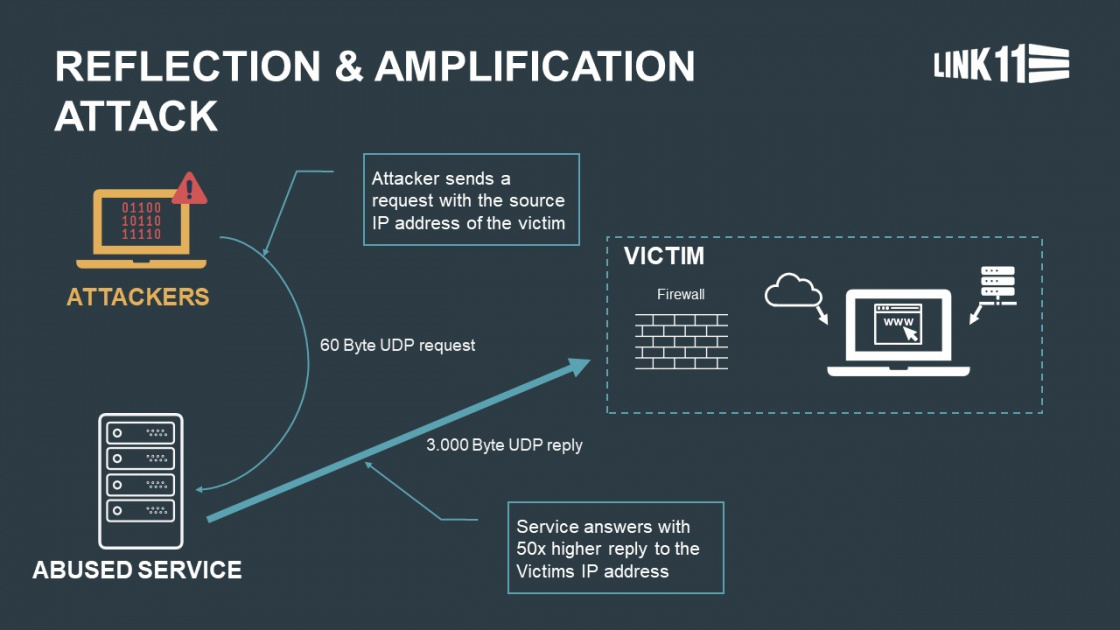
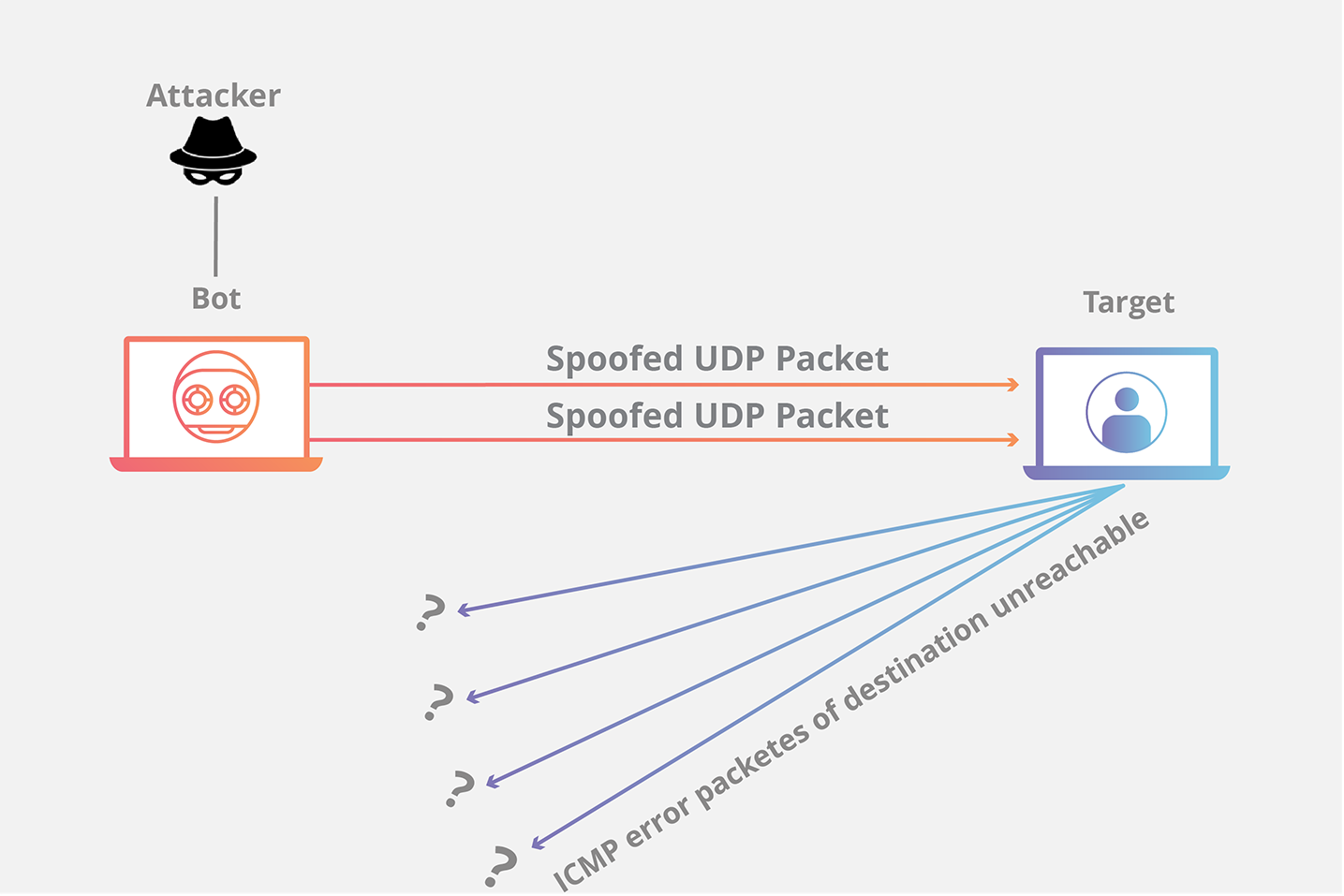
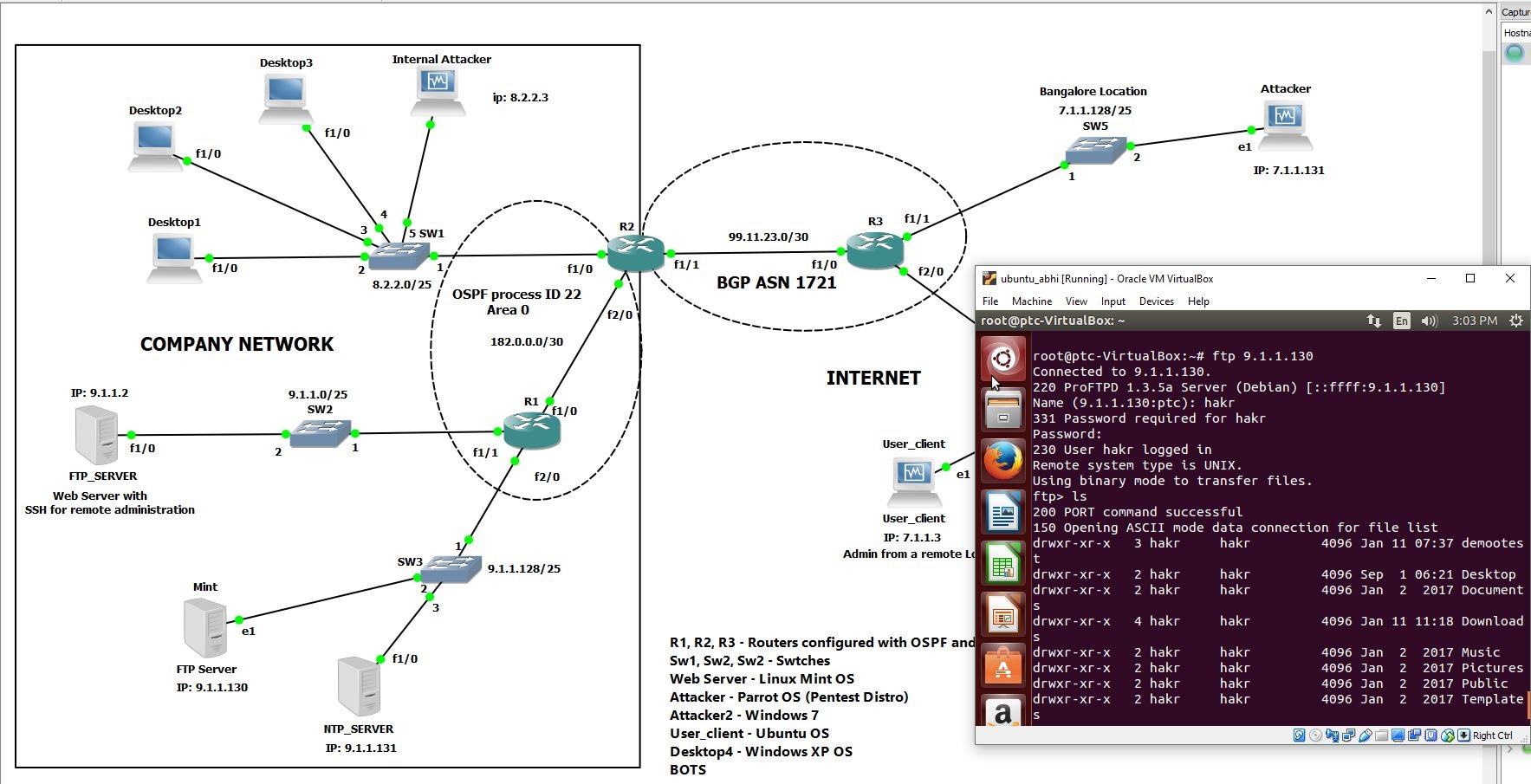
Detection and Analysis of TCP-SYN DDoS Attack in Software-Defined Networking | Wireless Personal Communications

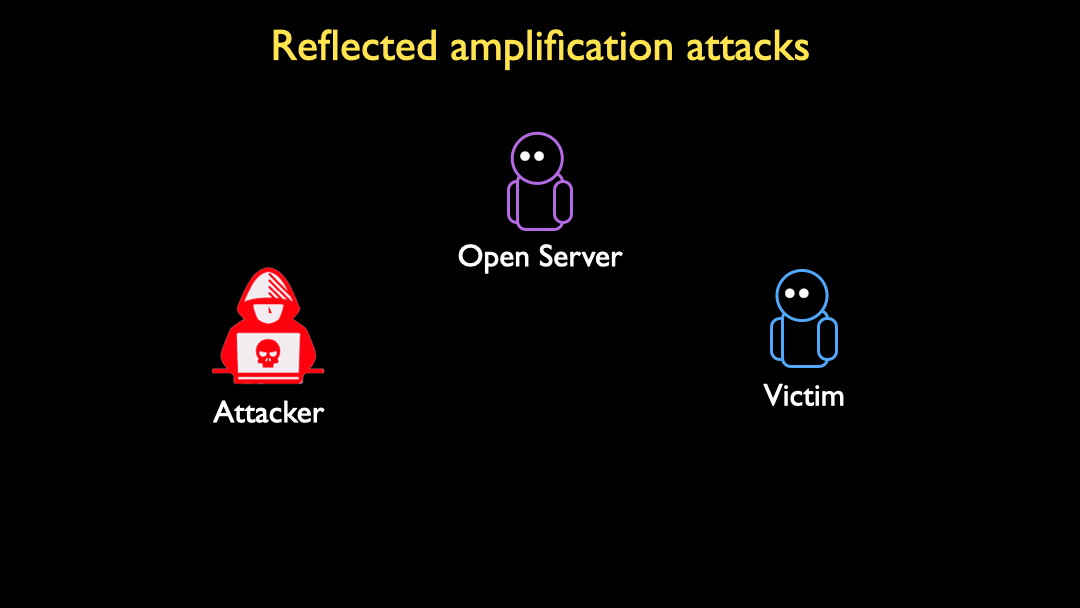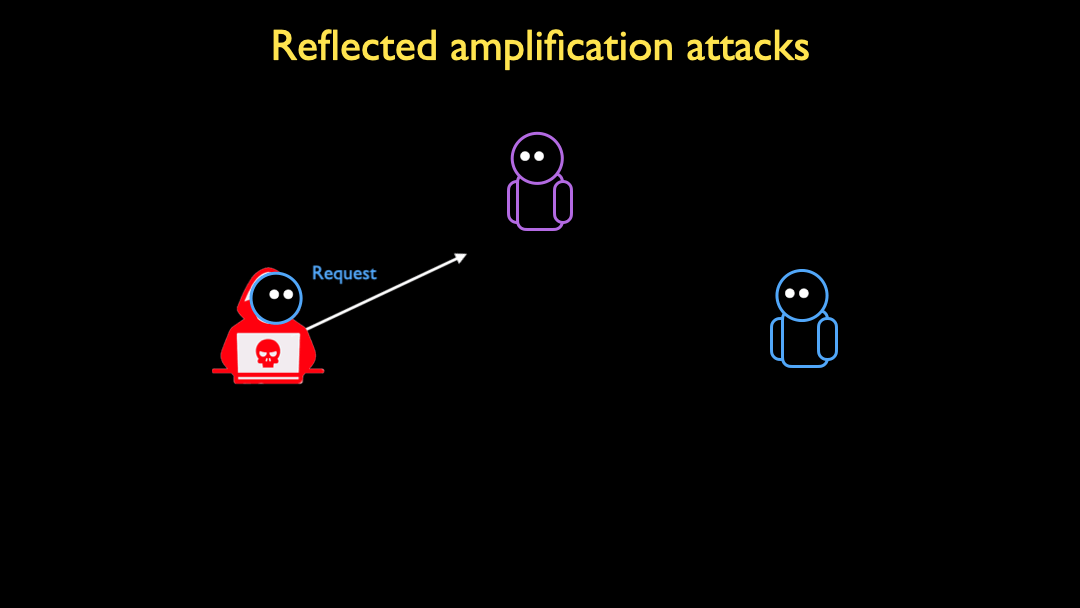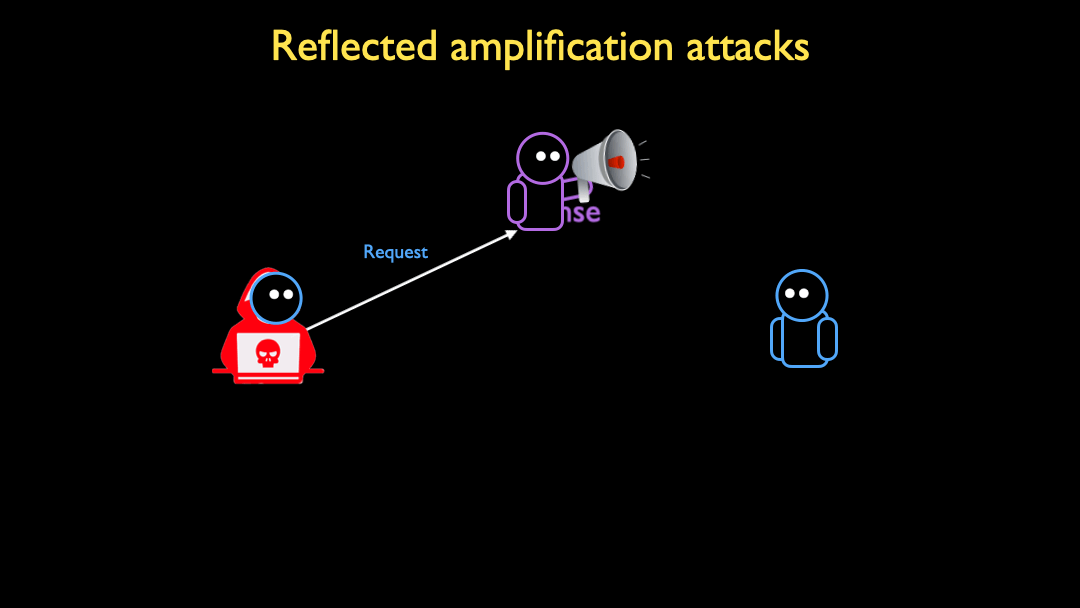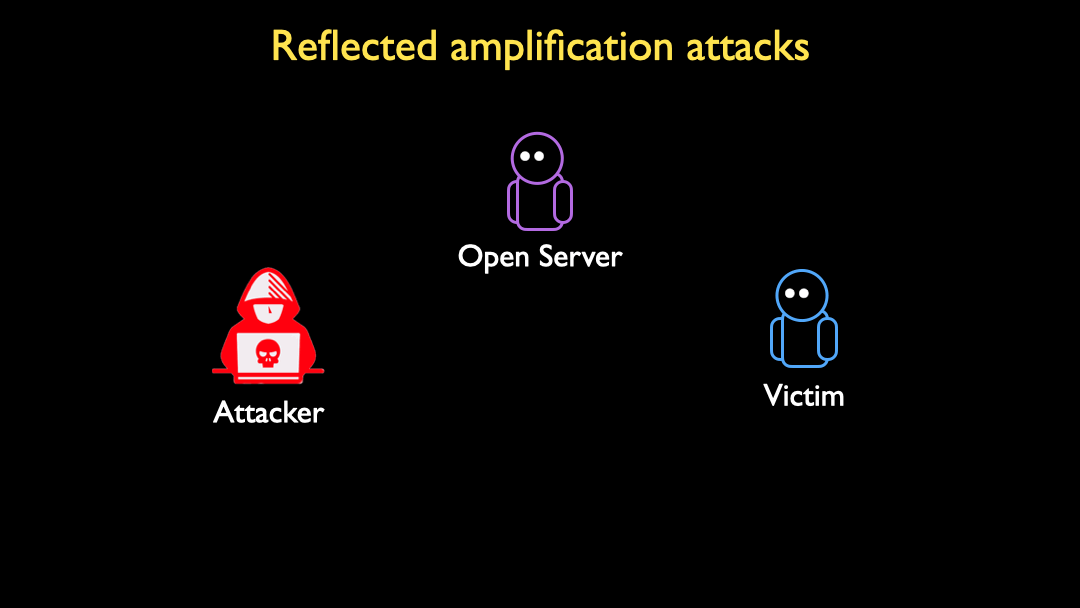
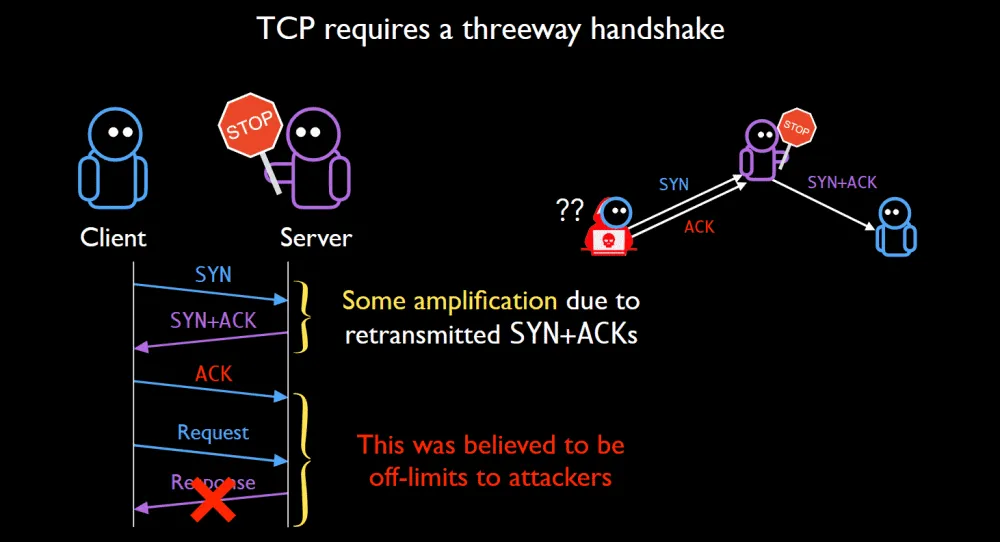
Research and Analysis of Middlebox-based TCP Reflective Amplification Attacks - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.
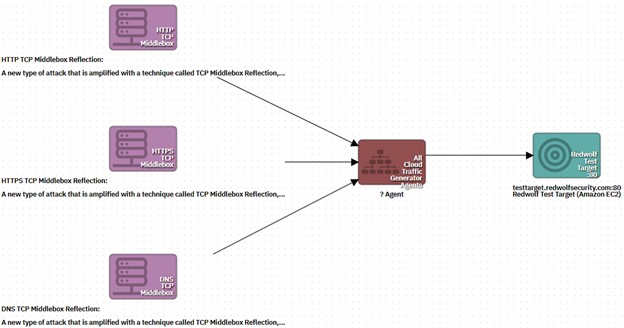
Understanding and Running “Middlebox TCP Reflected Amplification Attacks” with the RedWolf Platform - RedWolf Security Inc.