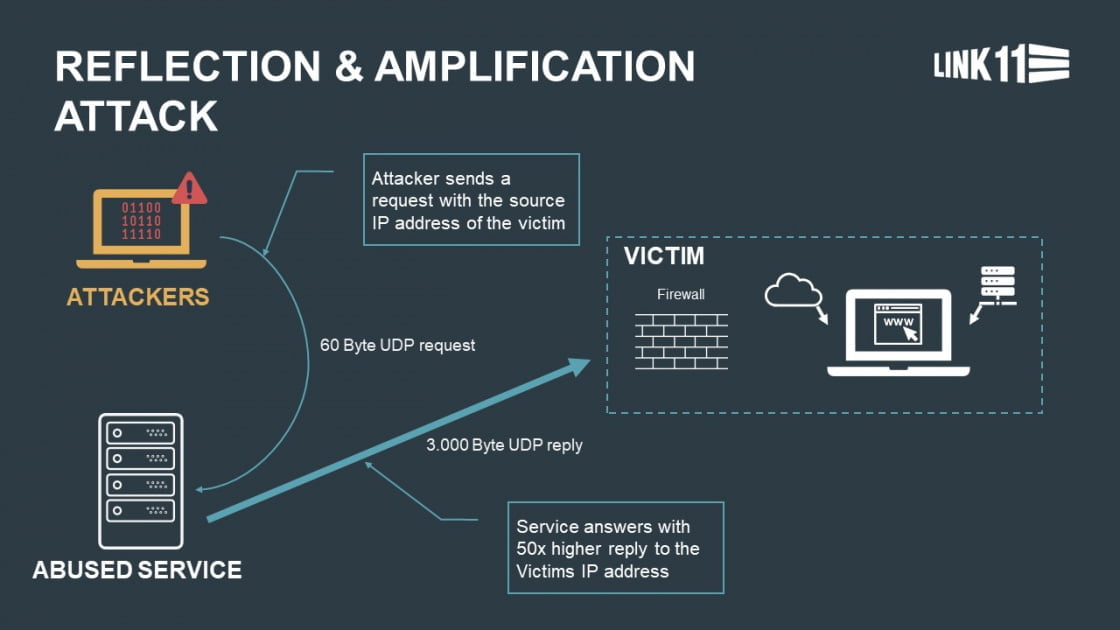
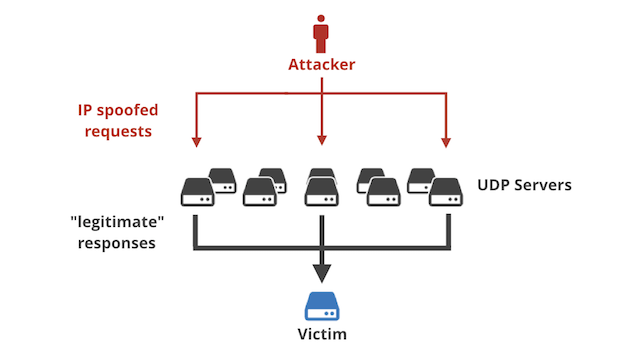
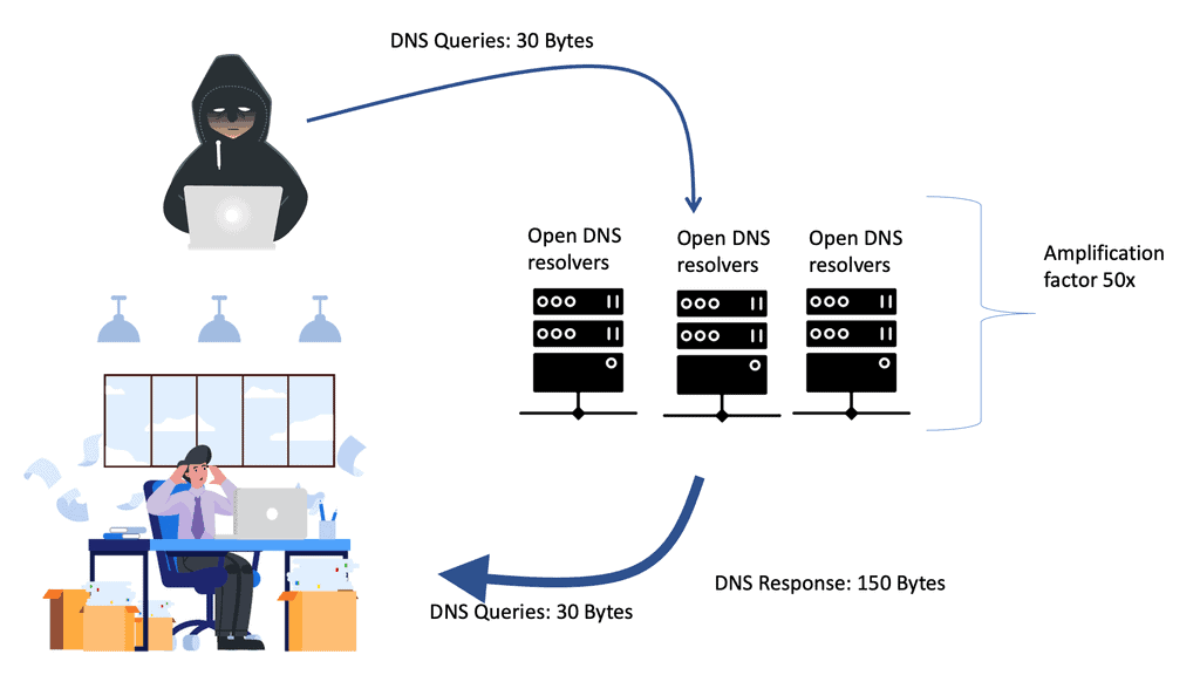
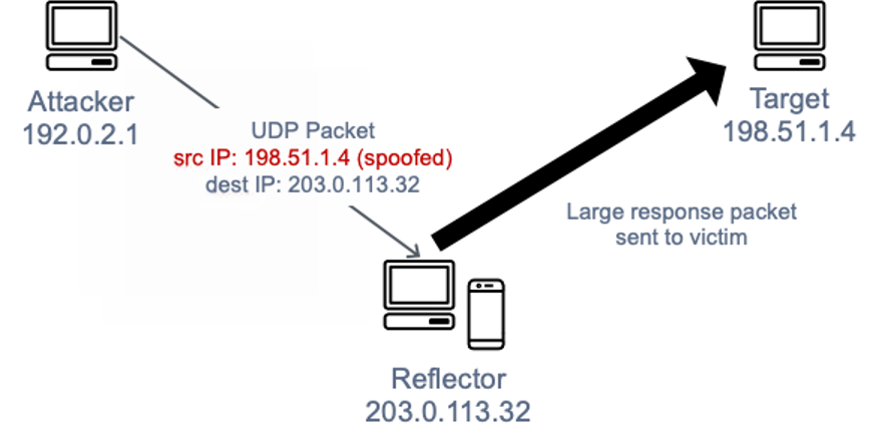
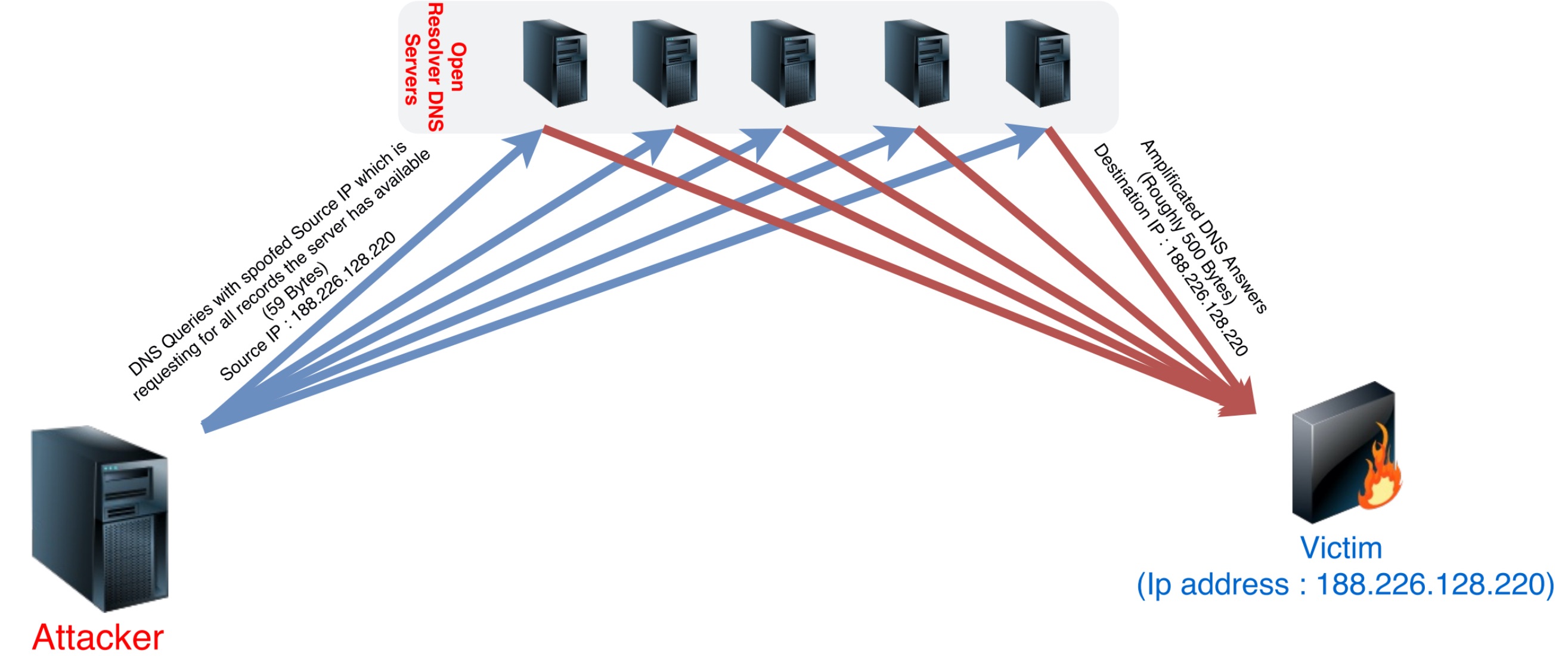
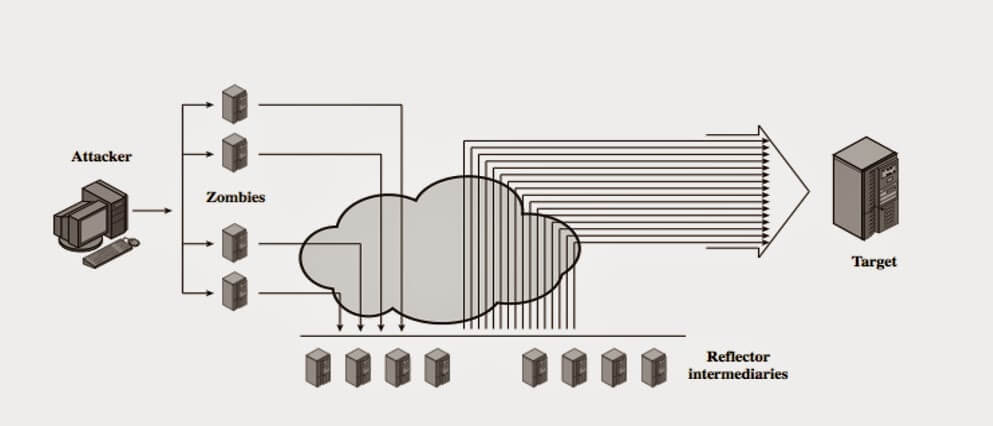
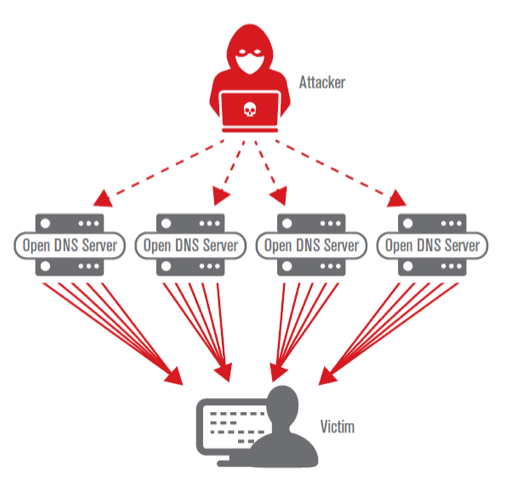
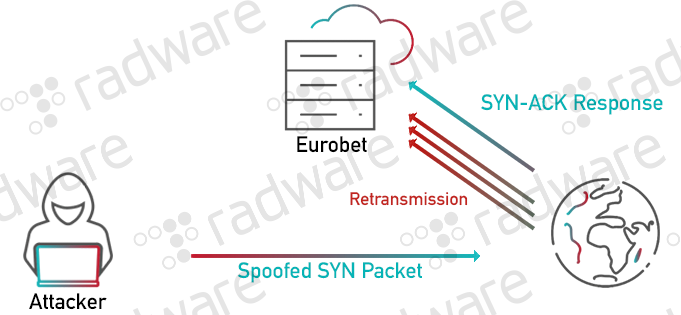
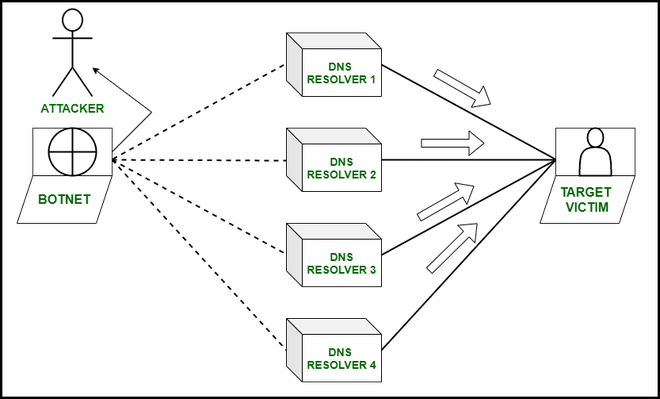
A reflection‐amplification Distributed denial of service (DDoS) attack... | Download Scientific Diagram
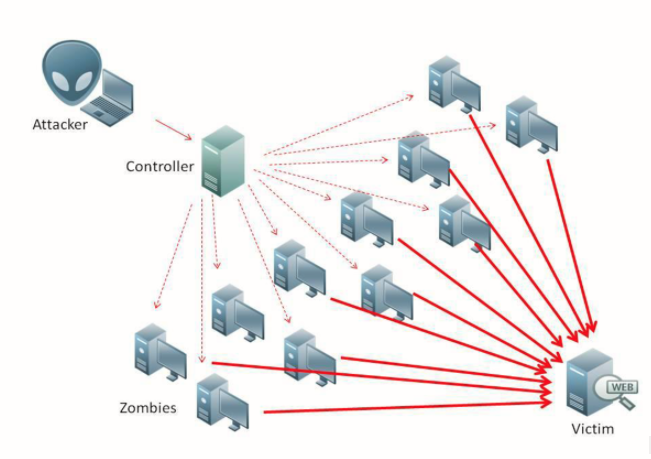
Nexus Intelligence Insights CVE-2020-2100: Jenkins - UDP Amplification Reflection Attack Leading to Distributed Denial of Service (DDoS)