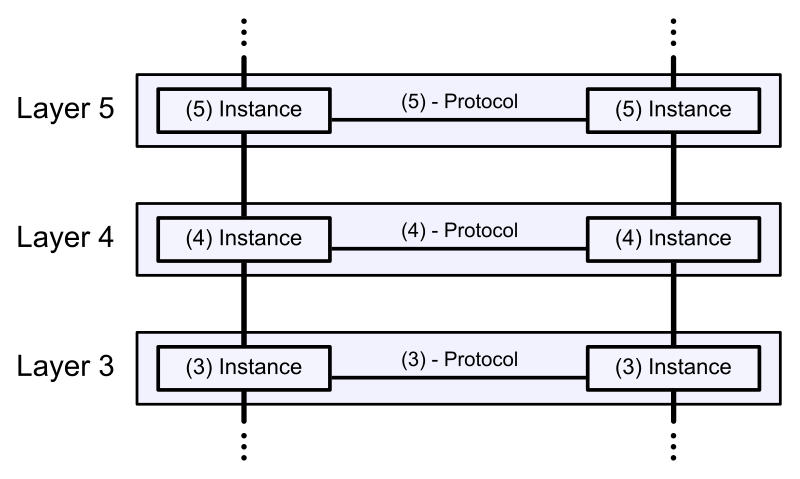
Figure 1 from A hardware accelerator for the IEEE 802.1X-2010 key hierarchy in automotive applications | Semantic Scholar

CISSP PRACTICE QUESTIONS – 20210804 by Wentz Wu, ISSAP, ISSEP, ISSMP CISSP, CCSP, CSSLP, CGRC, SSCP, CC, CISM, CISA, CRISC, CGEIT, PMP, ACP, PBA, RMP, CEH, ECSAWentz Wu

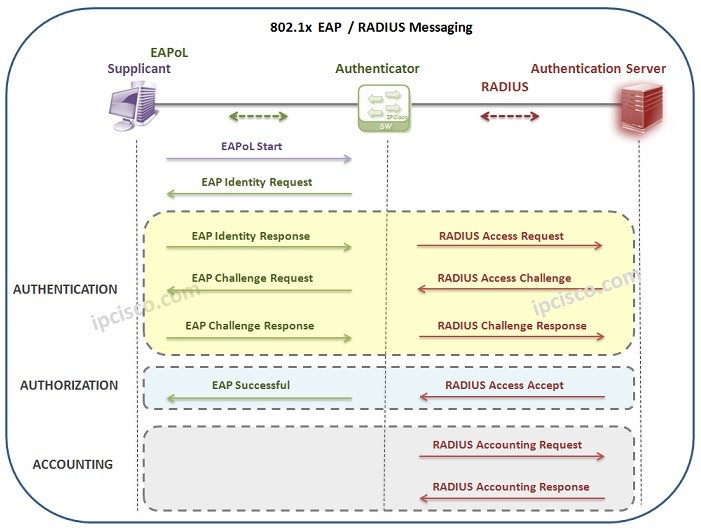



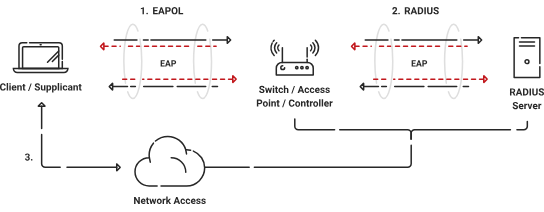
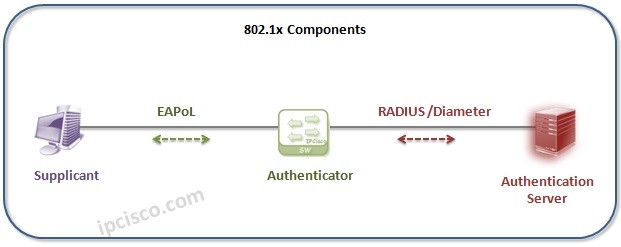
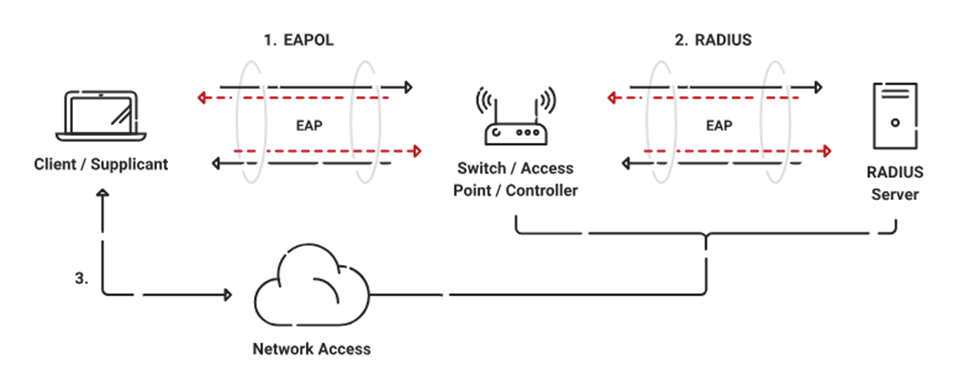

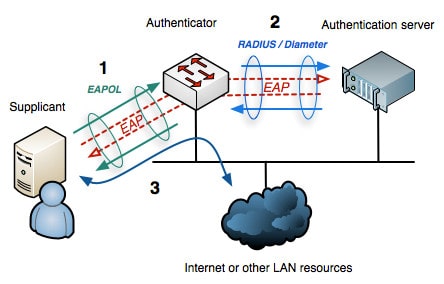
![802.11] Wi-Fi Security Concepts - NXP Community 802.11] Wi-Fi Security Concepts - NXP Community](https://community.nxp.com/t5/image/serverpage/image-id/126829iBFDDB78FEC391FFD/image-size/large?v=v2&px=999)